Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Protecting Your Network from Cyber Attacks
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights
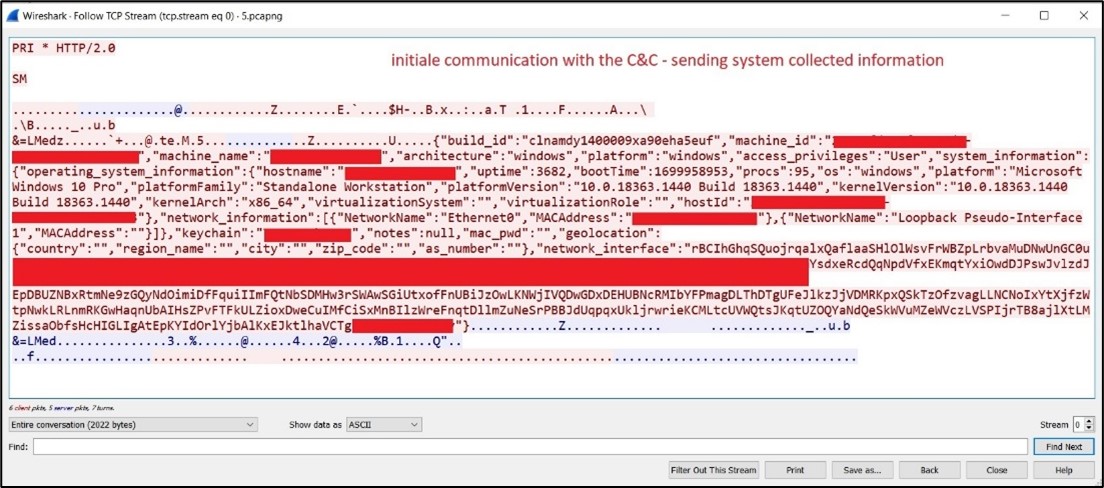
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog

A detailed analysis of the Menorah malware used by APT34
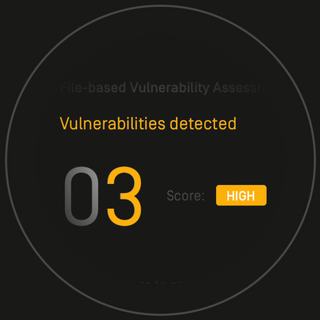
MetaDefender Cloud Advanced threat prevention and detection

Malware Analysis: Steps & Examples - CrowdStrike

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

What is Malware? Definition, Types, Prevention - TechTarget
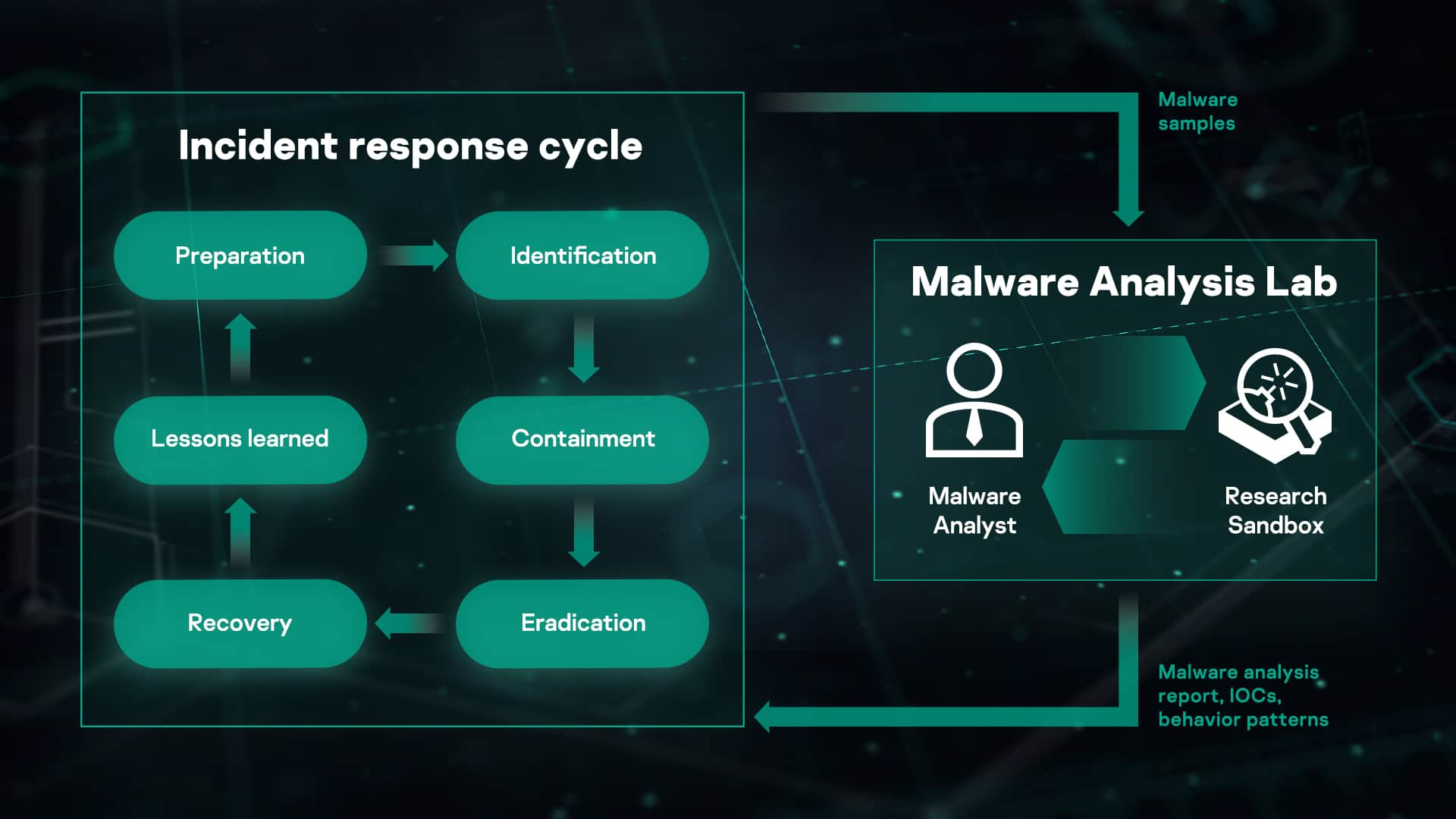
Advanced Automated Malware Analysis – Kaspersky Research Sandbox
de
por adulto (o preço varia de acordo com o tamanho do grupo)