Hackers Using New Obfuscation Mechanisms to Evade Detection
Por um escritor misterioso
Descrição
Recently, Microsoft has unveiled details of a deceptive social engineering campaign, in which the operators proceeded to change their obfuscation

Enterprise data breach: causes, challenges, prevention, and future

Google Ads Spread Detection Evading Malware - SecureTeam

How to Detect Obfuscated Malware on Your Server

Building coping mechanisms to deal with ransomware attacks across

Inside Cyber Attackers' Latest Efforts to Evade Detection
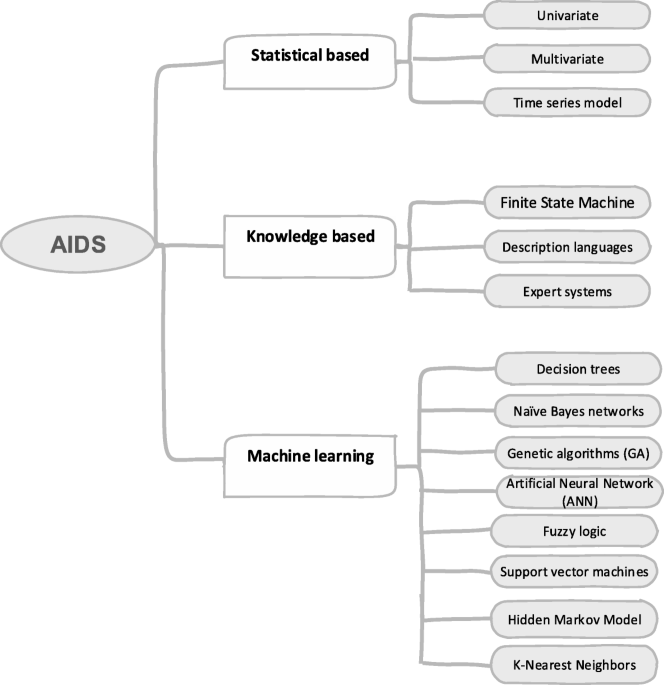
Survey of intrusion detection systems: techniques, datasets and

New JSSLoader Variant Uses XLL Files to Evade Detection

CB16] Invoke-Obfuscation: PowerShell obFUsk8tion Techniques & How
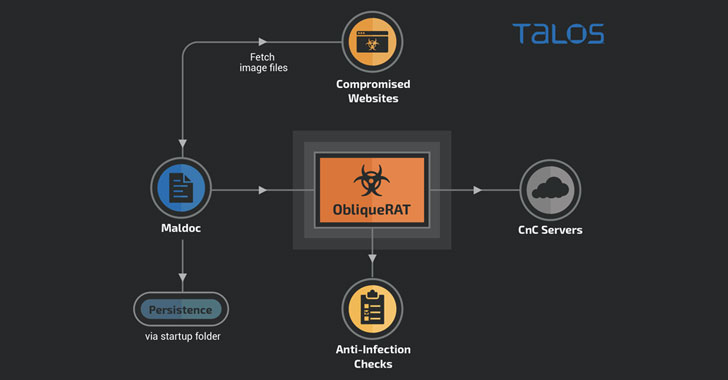
Hackers Now Hiding ObliqueRAT Payload in Images to Evade Detection

BGP Hijacking: How Hackers Circumvent Internet Routing Security
Hackers Use 'URL Obfuscation' Technique to Deliver Malware
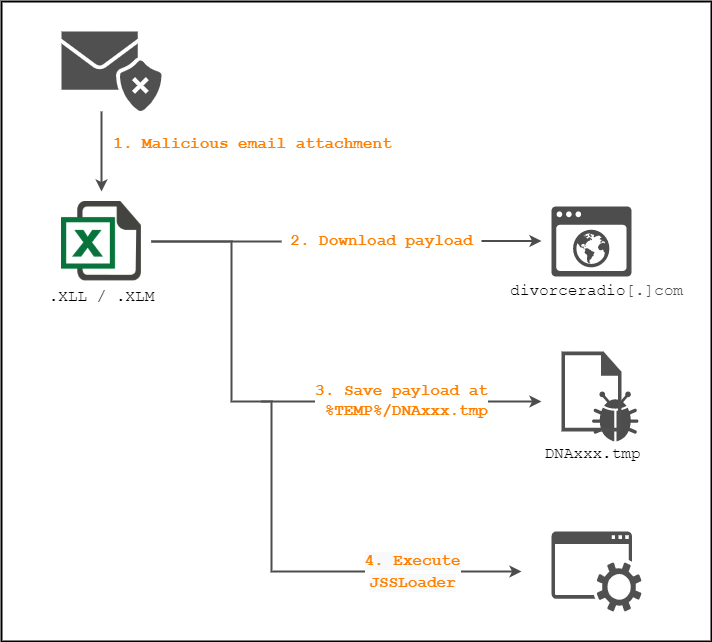
New JSSLoader Trojan Delivered Through XLL Files
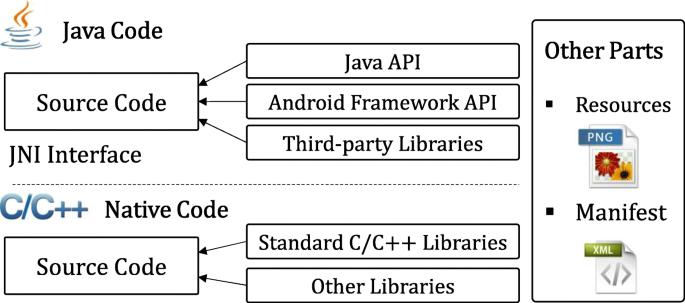
Layered obfuscation: a taxonomy of software obfuscation techniques
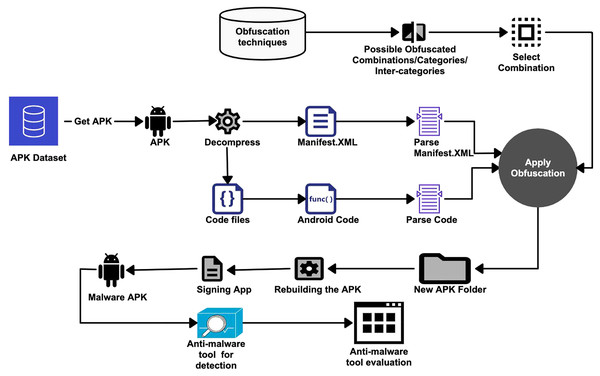
On the evaluation of android malware detectors against code
de
por adulto (o preço varia de acordo com o tamanho do grupo)







